NIS 2 Compliance Without the Migraine
Finally, a cybersecurity assistant that actually gets NIS 2 Directives and local adoptions
Stop drowning in spreadsheets and compliance theater.
WINGMAN turns your regulatory headache
into a manageable conversation.

The NIS 2 Reality Check
Your Current Compliance Situation Looks Like This:
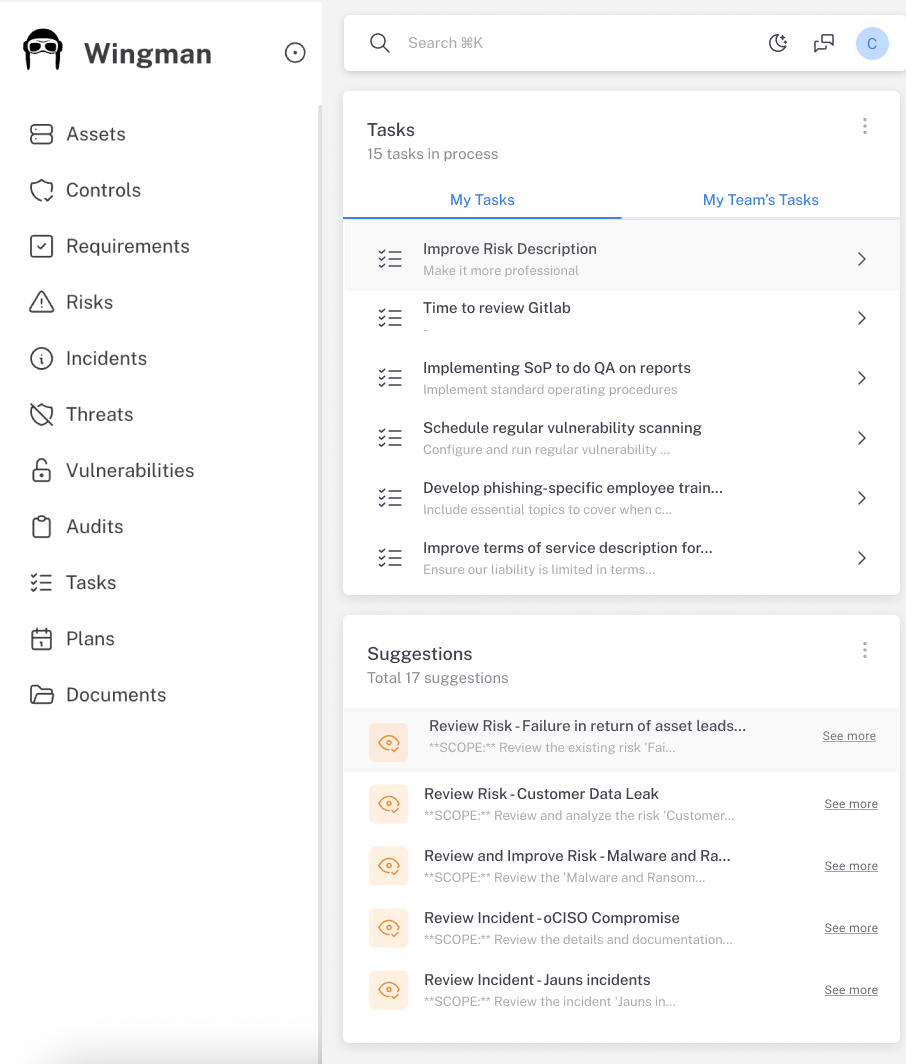
Typical Compliance Dashboard
Compliant
127
Non-Compliant
43
Needs Review
29
Not Assessed
156
Framework Compliance Status
NIS 2 Directive
ISO 27001:2022
Recent Activities
Analogy:
It's like being asked to paint the Mona Lisa while riding a unicycle, blindfolded, with paintbrushes made of spaghetti. Sure, it's technically possible, but wouldn't you prefer actual art supplies?
Why Traditional Tools Make It Worse
The Tool-Stacking Tragedy
The Security Tool Zoo
- Your EDR/XDR finds threats but can't tell you which compliance requirements they violate
- SIEM generates 10,000 alerts but can't prioritize based on your actual risk register
- Vulnerability scanners discover issues but can't map them to your documented asset inventory
- Penetration test reports sit in folders, disconnected from your ongoing security operations
- Your superadvanced IDS sits on the shelf and has never been actually connected to network traffic
The Documentation Scavenger Hunt
- NIS 2 policies live in SharePoint, incident response procedures are in Confluence, asset lists are in Excel somewhere
- Security standards scattered across internal wikis, intranet sites, and that one person's Google Drive
- When someone asks "where's our backup policy?" the answer is genuinely "good question"
- New team members spend weeks hunting for documentation that may or may not be current
- Risk assessments reference procedures that exist in 3 different versions across 4 different systems
The Integration Illusion
- Each tool has its own dashboard, its own priorities, its own definition of "critical"
- Security team spends more time translating between tools than actually securing things
- Compliance dashboards showing green while actual security looks like a house of cards in a hurricane
- Risk assessments that ignore what your security tools are actually telling you
The Data Disconnect
- Your beautiful GRC system doesn't know about last week's incident response
- Asset inventory says "Server-001" but your monitoring tools call it "prod-web-03"
- Policies describe controls that your technical tools can't verify are working
- Compliance reports reference systems that were decommissioned months ago

The Prioritization Paralysis
- Critical vulnerability from scanner or compliance gap from audit?
- Security incident response or NIS 2 documentation update?
- Actual security improvement or explaining to auditors why your tools don't match your documentation?
Meet WINGMAN - Your Compliance Translator
Built on 20+ Years of Real-World Experience
Like Having a Senior CISO Who Never Sleeps
Maintains Living Security Context
Not static spreadsheets that lie to you. Real-time awareness of what's connected to what.
Automates the Boring Compliance Stuff
Automatically tracks changes to your asset inventory. Generates risk assessments that actually reflect reality.
Prioritizes What Actually Matters
"Hey, that new server you deployed affects 3 NIS 2 requirements and 2 risk assessments"
.png)
Real NIS 2 Scenarios Where WINGMAN Saves the Day
Document Gap Analysis
Problem: You have cybersecurity policies but suspect they don't cover all NIS 2 requirements
With WINGMAN: "I analyzed your current documentation against NIS 2 requirements. Here are 7 gaps, 3 conflicting policies, and 12 technical controls that exist in theory but not in practice."
New System Deployment
Problem: Your team deploys new customer portal
With WINGMAN: "I noticed the new portal during attack surface scan. Here's the updated compliance docs and 3 risks we should discuss."
Incident Response Reality Check
Problem: Potential security incident detected by EDR
With WINGMAN: "This affects Class A systems per your asset register, meets NIS 2 reporting thresholds, here's the CERT-LV notification draft."
How WINGMAN Works With Your Existing Tools
The Central Intelligence Approach
WINGMAN doesn't replace your EDR, SIEM, or vulnerability scanners—it makes them actually work together. Think of it as the translator who finally gets your security tools talking to your compliance requirements.
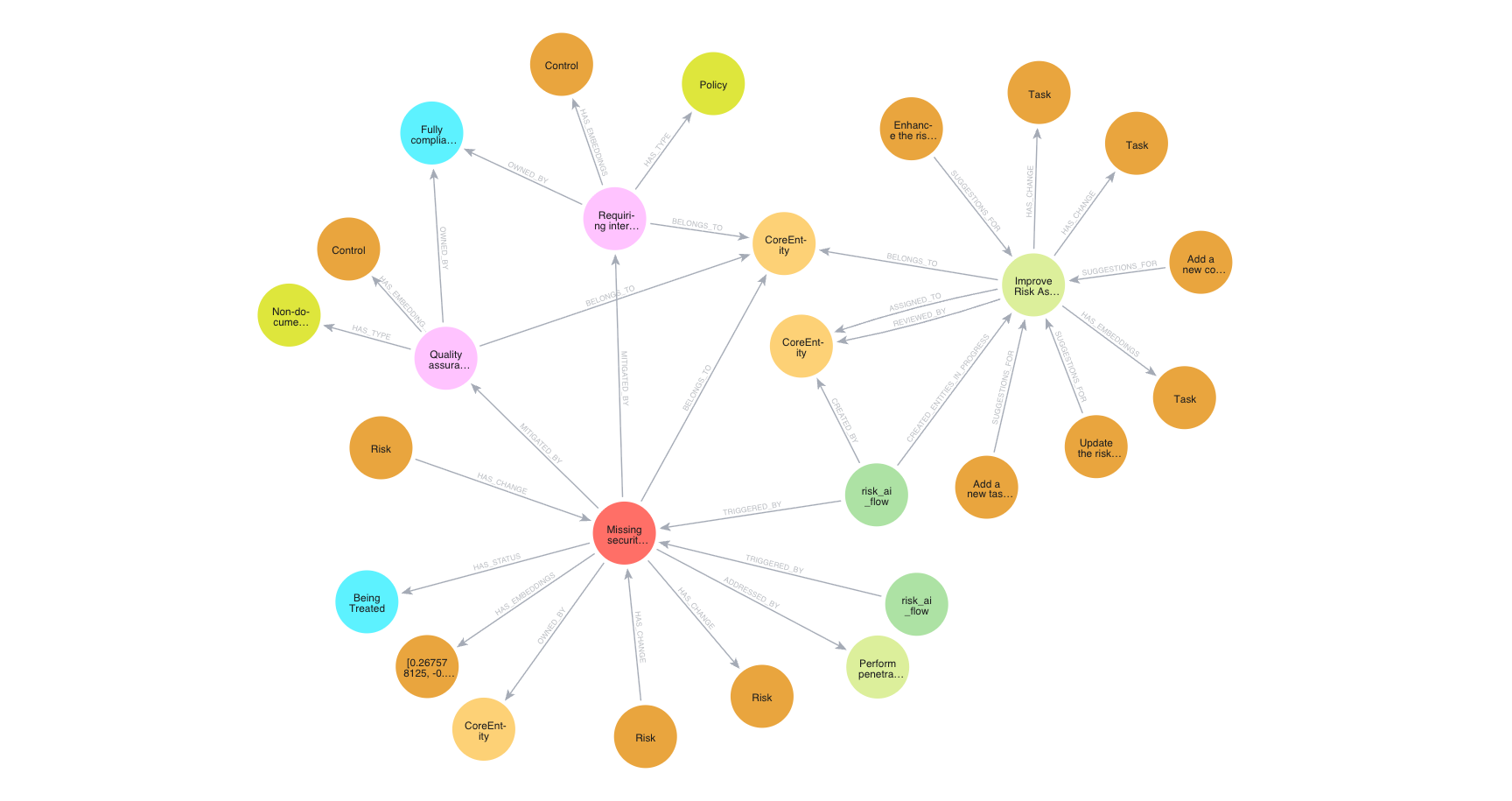
WINGMAN graph showing EDR vulnerability report connecting to specific asset, related risks, and relevant NIS 2 requirements
Nodes & Relationships Architecture
Nodes
Everything that matters (assets, vulnerabilities, incidents, policies, requirements, controls)
Relationships
How they actually connect in real life (not just in documentation)
AI Flows
Smart automation that keeps everything current and actionable
Tools
Smaller AI driven tools to improve and maintain data quality
Your Tools, Supercharged
EDR/XDR Integration
"This endpoint threat affects Asset-X, which handles Class A data per MK 397, here's the required response timeline"
SIEM Enhancement
"These 47 alerts relate to the same compliance gap, here's the single action that fixes them all"
Vulnerability Management
"This scanner finding affects 3 systems in your asset registry, impacts 2 NIS 2 requirements, priority: actual high"
Task Management
"Tasks in JIRA created, updated and retrieved by Wingman to allow invisible progress checking without jumping between multiple windows/tools"
Your Life After WINGMAN
Compliance Becomes Boring (In the Best Way)
Monthly Reviews
"WINGMAN, show me what changed this month" → instant compliance status
Risk Assessments
Actually current, automatically updated, defendable to auditors
Annual Reports
Generated in minutes, not months, gathering real state of affairs
Incident Response
Clear guidance instead of panicked googling, all information in one place
Getting Started Without the Usual Implementation Hell
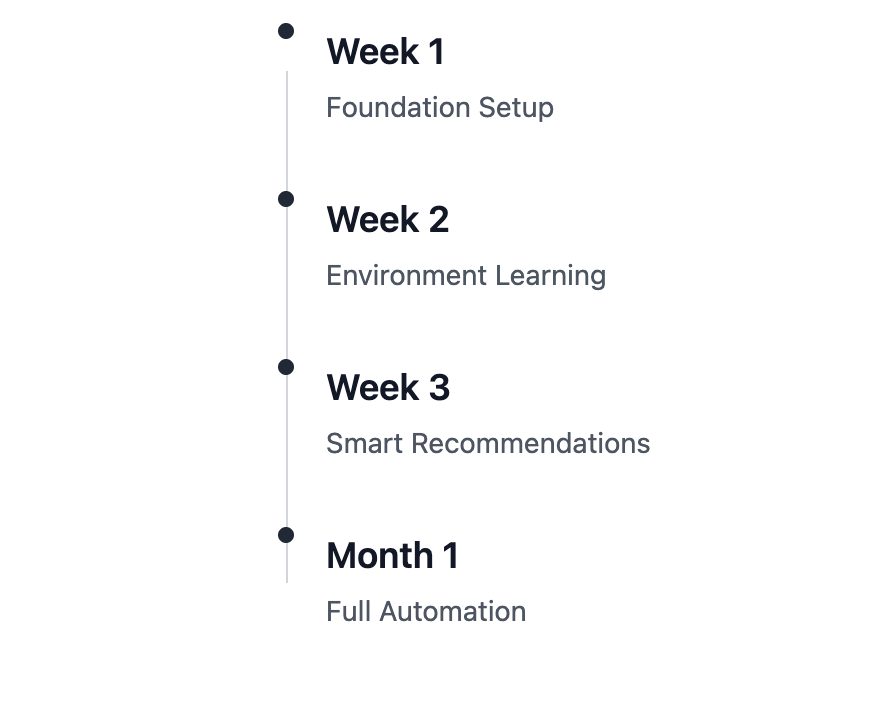
What Happens Next
Week 1
Connect your existing tools, import current asset inventory, policies and procedures, build understanding of controls and relationships
Week 2
WINGMAN learns your environment, provides first compliance gap analysis against NIS 2 and local regulations
Week 3
Start getting actionable recommendations instead of red/green lights, first risk assessment
Month 1
First automated compliance report that actually reflects reality, support during incident responses, vulnerability handling automation, available to all employees 24x7 to answer security questions and provide awareness guidance
Pricing That Makes Sense
Think of it as hiring a senior cybersecurity analyst who:
Never takes vacation during compliance season
Remembers every detail of every system
Speaks fluent local regulations and EU regulation
Works 24/7 without coffee breaks
Costs less than half a FTE salary
Still Have Questions?
Common Concerns (And Honest Answers)
How do we know this won't become another abandoned compliance tool?
This is like moving your things around in your house 3 times before buying shelves. Wouldn't it be easier to put shelves in place and just put things where they belong? Same way it is much easier to get things in order with WINGMAN and once they are there, every next step just takes less. Stop fighting fires and move into planned improvement mode.
Will this replace our existing tools?
No. WINGMAN makes your existing tools actually useful. Think of it as adding subtitles to a foreign film instead of learning a new language.
What if our setup is too unique/complex/weird?
We've worked with organizations running everything from cutting-edge cloud to systems older than some of our team members. If it processes data, WINGMAN can work with it.
How do we know this won't become another abandoned compliance tool?
Because it's designed by people who've actually done CISO work, not just sold software to CISOs. We use it ourselves, which tends to keep things practical.
What Previous Demo Attendees Say:
"Finally, someone who understands that compliance isn't about perfect documentation — it's about connecting what we actually do with what we're supposed to document."
"The demo showed us gaps we didn't even know we had. More importantly, it showed us how to fix them without buying more tools."
Ready to Stop the NIS 2 Compliance Madness?
Book Your WINGMAN Demo - Show Me How This Solves My NIS 2 Headaches
What You Get in Your Demo:
Live analysis of your current NIS 2 compliance gaps using WINGMAN
Your actual security tools integrated with regulatory requirements (not generic examples)
Specific implementation timeline and approach for your organization
45 minutes with people who've actually implemented this stuff, not sales theater
Demo Format:
- Bring your current compliance challenges (asset inventories, risk registers, policies)
- We'll show WINGMAN analyzing your actual documentation and finding real gaps
- See how your existing EDR/SIEM/scanner outputs connect to NIS 2 requirements
- Leave with a practical action plan, not just pretty screenshots
